Categories
Recent Stories

Essential Pen Testing Software for Cybersecurity
Nov 6, 2024 Information hub
Pen testing software automates vulnerability detection, securing systems against cyber threats. Learn its types, benefits, and latest trends to boost your cybersecurity.

Open Source Vulnerability Scanner for Stronger Security
Nov 6, 2024 Information hub
Learn how open source vulnerability scanners help detect security risks. From features to benefits, find out how these tools strengthen cybersecurity in any business.
Understanding CERT Information Security
Nov 6, 2024 Information hub
Explore CERT Information Security's role in managing and preventing cyber threats. From incident response to threat intelligence, discover how CERTs keep systems safe.
What is OWASP? A Guide to Web Application Security
Nov 6, 2024 Information hub
Discover OWASP, a key resource in web security. This guide covers OWASP's mission, the Top 10 risks, tools like ZAP, and trends in application security.
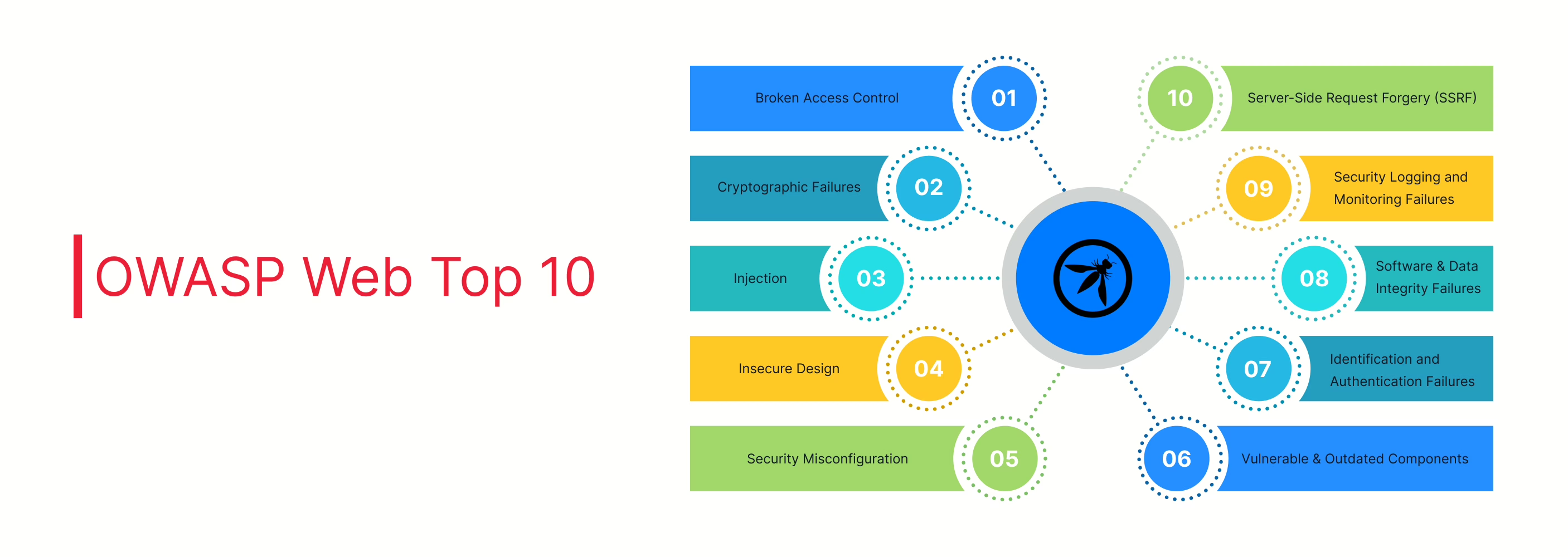
OWASP Web Top 10: Key Risks for Securing Web Apps
Nov 6, 2024 Information hub
Learn about the OWASP Web Top 10, a list of key web security risks. Discover how to secure web applications with examples, solutions, and preventive tips.
Understanding Test Injection SQL: Protect Your Database
Nov 6, 2024 Information hub
Discover the risks of SQL injection, a major threat to databases today. Learn how attacks work and get essential tips on preventing SQL injection for stronger database security.

Why SQL Vulnerability Test is Essential for Data Security?
Nov 6, 2024 Information hub
An SQL vulnerability test detects weaknesses in databases to prevent cyberattacks and data breaches. Learn how it helps organizations stay secure, compliant, and build customer trust.

What is Static Code Analysis: Boosting Code Quality & Security
Nov 6, 2024 Information hub
Learn what static code analysis is, why it's essential for boosting code quality, reducing bugs, and enhancing security in development. Explore benefits, tools, and future trends to optimize your software process.










