It seems we can’t find what you’re looking for. Perhaps searching can help.
Categories
Recent Stories
Recent Stories

Intellect Vulnerability: Mitigating CVE-2015-6540
May 20, 2024 Bug hunting
Securityium identified a critical XSS vulnerability, labelled as CVE-2015-6540, in Intellect Core banking software, allowing attackers to execute harmful JavaScript code. Immediate action is needed to mitigate this threat.

Securityium Discovers Major Arlo Vulnerability
May 20, 2024 Bug hunting
In cybersecurity, mere compliance with industry standards is no longer sufficient to protect your organization from the m.

Synology Vulnerabilities: A Critical Security Flaw
May 20, 2024 Bug hunting
Securityium uncovered critical vulnerabilities in Synology's systems, including unauthenticated file uploads and an SSRF flaw, highlighting the need for continuous vigilance and proactive cybersecurity measures.

A Critical Netgear Vulnerability: CVE-2021-29069
May 20, 2024 Bug hunting
Securityium identified a vulnerability in certain Netgear routers, officially labeled as CVE-2021-29069. This flaw, rooted in insufficient validation within the email module, exposes affected devices to severe command injection attacks.
Why Multiple Pentesting Vendors are Essential?
May 30, 2024 Information hub
Multiple pentesting vendors enhances security by finding diverse vulnerabilities, ensuring frequent testing, optimizing resources, and gaining a competitive edge through bakeoffs.

Secure Your Software: SAST & DAST Cyber Strategies
May 31, 2024 Information hub
Penetration Testing for Web & Mobile Security
May 31, 2024 Information hub
Penetration testing, also known as a pen test, is a simulated cyber attack against your computer system to check for exploitable vulnerabilities. In the context of web and mobile application security, penetration testing is commonly used to uncover vulnerabilities.

Banking Cybersecurity: Pen Testing Essentials
May 31, 2024 Information hub
In the modern digital era, the banking industry heavily relies on technology and interconnected systems to provide efficient and convenient financial services to customers. However, this reliance on technology also exposes the banking sector to various cyber threats
GoLang Security Best Practices: Secure Your Code
May 31, 2024 Information hub
Discover how to enhance your GoLang code security with comprehensive checks and validations from the Go Secure Coding Practices Guide. Learn about key areas like input validation, output encoding, authentication, and more.
Strengthen Software Security with SCA
May 31, 2024 Information hub
Enhance your software security and ensure compliance with Securityium's Software Composition Analysis (SCA) services. Identify and address security flaws, licensing compliance issues, and code quality concerns related to open source software.

Unmasking Cybersecurity Trends: New Threats Revealed
May 31, 2024 Information hub
In the fast-evolving digital landscape, the realm of cybersecurity continues to face ever-changing challenges. As technology advances, so do the methods and sophistication of cyberattacks.

Cyber Security Threats: Prepare & Protect
May 31, 2024
The Hidden Vulnerabilities VA/PT Can Uncover
May 31, 2024
Strengthen Your Cyber Defense with VA
May 31, 2024 Information hub

Safeguard Against Insider Threats: Top 5 Strategies
May 31, 2024 Information hub
The human element remains both the greatest advantage and the most critical weakness in the continuously growing field of cybersecurity. As business leaders and key decision-makers, your role in steering your organisation toward success is undeniable.
VA/PT: Crucial in Modern Cybersecurity
May 31, 2024 Information hub
The need for effective defense measures has never been more vital in the ever-changing landscape of cybersecurity, where threats continue to grow in complexity and frequency.

Boost Security Beyond Compliance with VAPT
May 31, 2024 Information hub
Ony compliance with industry standards is no longer sufficient to protect your organization from the multifaceted threats that lurk in the digital shadows.

From Risk to Resilience VAPT Insights
May 31, 2024 Information hub
Explore VAPT’s transformative journey from risk to resilience with Securityium, uncovering vulnerabilities, fortifying defenses, and achieving robust cybersecurity.

Adapting Cybersecurity: Trends & Strategies
May 31, 2024 Information hub
Explore the evolving threatscape and learn how Securityium helps you adapt your cybersecurity strategy to stay ahead of cyber threats and protect your digital assets.

Penetration Testing: Cybersecurity Essentials
May 31, 2024 Information hub
Uncover how Penetration Testing fortifies cybersecurity. See how Securityium identifies vulnerabilities and strengthens your digital defenses for proactive protection.
Protecting Sensitive Data in Industries
Jun 6, 2024 Information hub
Explore the vital role of penetration testing in safeguarding sensitive data across diverse industries and mitigating risks of data exposure in today's digital landscape.
The Importance of Pentesting in Modern Cybersecurity
Jun 13, 2024 Information hub
Penetration testing (pentesting) is crucial for strengthening IT infrastructure against cyber threats by simulating attacks and identifying vulnerabilities.
Preventing Phishing-Induced Data Breach
Jun 20, 2024 Information hub
Prevent data breaches with Securityium's insights on phishing risks, breach causes at Dropbox, and proactive cybersecurity measures.
Vendor Impersonation Threat in IT Security
Jun 27, 2024 Information hub
Protect your business from phishing attacks with Securityium's insights on preventing cyber threats through robust IT security measures and training.
Supply Chain Management in Cybersecurity
Jul 4, 2024 Information hub
Protect your business from supply chain attacks with Securityium's comprehensive strategies and insights on mitigating cybersecurity risks effectively.

Understanding Incremental Penetration Testing
Aug 9, 2024 Information hub
An Incremental Penetration Test is an approach of security testing that focuses specifically on evaluating the security of new or modified features in an application since the last full penetration test.
The Cybersecurity Shield – Attack Surface Scan
Aug 23, 2024 Information hub
Enhance your cybersecurity with attack surface scanning. Discover vulnerabilities, safeguard digital assets, and ensure compliance. Explore our blogs for such proactive strategies.
A Vulnerability in reNgine: CVE-2024-43381
Aug 26, 2024 Bug hunting
Learn about CVE-2024-43381, a Stored XSS vulnerability in reNgine. This article covers how the flaw works, its potential risks, and key strategies to mitigate the threat.
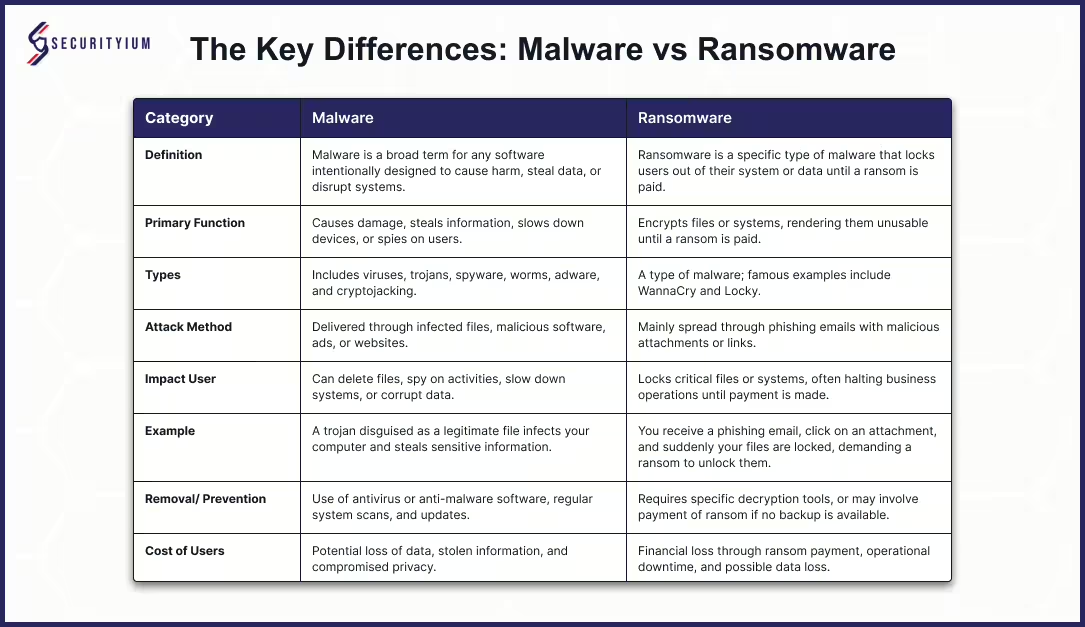
Malware vs Ransomware: Unmasking the Key Differences
Oct 8, 2024 Information hub
Learn the differences between malware and ransomware, their attack methods, and effective prevention strategies to safeguard your data.
Viruses vs. Worms vs. Trojan Horses: A Detailed Guide With Prevention Tips
Oct 11, 2024
Explore the distinctions between viruses, worms, and Trojan horses in this guide. Understand how each operates, with examples, and learn essential cybersecurity tips for staying protected.

GDPR and Small Businesses: A Simple Guide to Compliance and Benefits
Oct 15, 2024
Discover how GDPR affects small businesses, key compliance steps to follow, and the long-term benefits of data protection. Ensure your business meets GDPR standards and builds customer trust.

GDPR for Small Businesses: A Practical Guide to Compliance
Oct 15, 2024 Information hub
This guide on GDPR for small businesses explains its importance, challenges, and simple steps to comply with data privacy laws, safeguarding your business from fines and protecting customer data.
Compliance with GDPR: Essential Steps for Protecting Data in 2025
Oct 15, 2024 Information hub
Discover why compliance with GDPR is crucial in 2025. Learn practical steps to protect personal data, avoid hefty fines, and build trust with your customers.

How Businesses Can Comply to GDPR: A Complete Guide for Data Privacy and Protection
Oct 15, 2024 Information hub
Discover practical ways businesses can comply to GDPR, understand its importance, and explore the benefits of adhering to data privacy regulations for better security and customer trust.

Data Protection Compliance: Key Regulations, Trends, and Best Practices for Businesses
Oct 15, 2024 Information hub
Explore data protection compliance, the laws businesses must follow, and steps to ensure secure data management. Learn how staying compliant can protect your business and customers' trust.

GDPR Checklist: Essential Steps for Businesses to Ensure Data Protection Compliance
Oct 15, 2024 Information hub
This GDPR checklist outlines key steps for businesses to ensure data protection compliance, from consent and data audits to security measures, helping avoid fines and protect customer data.

GDPR Compliance Requirements: Key Steps for Businesses in 2025
Oct 15, 2024 Information hub
Discover the crucial GDPR compliance requirements your business must follow to protect data, avoid penalties, and build customer trust. A guide to help ensure compliance in 2025.

GDPR Requirements: Key Guidelines for Businesses to Ensure Compliance
Oct 15, 2024 Information hub
Learn about essential GDPR requirements, including data minimization, lawful processing, and data breach notifications, to help businesses stay compliant and safeguard personal data.

GDPR Compliance: Why It Matters for Your Business in 2024
Oct 15, 2024 Information hub
Discover the importance of GDPR compliance in today's world, practical tips for ensuring data protection, and how businesses can stay ahead in the evolving privacy landscape.

Essential General Data Protection Regulation Checklist for Business Compliance
Oct 15, 2024 Information hub
Discover the key steps to GDPR compliance with our General Data Protection Regulation checklist. Stay compliant, avoid fines, and enhance customer trust with simple, actionable tips.

How to Be GDPR Compliant: A Step-by-Step Guide for Businesses
Oct 15, 2024 Information hub
Discover how to be GDPR compliant with actionable steps. Ensure your business protects personal data and meets legal requirements to avoid penalties and enhance customer trust.

Pen Test vs Vulnerability Scan: Understanding the Key Differences in Cybersecurity
Oct 15, 2024 Information hub
Explore the key differences between pen test vs vulnerability scan. Learn how each method can strengthen your organization's cybersecurity strategy against evolving threats.

Penetration Testing vs Vulnerability Scanning: Key Differences Explained
Oct 15, 2024 Information hub
Explore the differences between penetration testing vs vulnerability scanning. Learn how both methods work together to enhance your organization's cybersecurity posture.

Strengthening Cybersecurity: The Importance of Vulnerability Assessment and Penetration Testing
Oct 15, 2024 Information hub
Discover the key benefits of Vulnerability Assessment and Penetration Testing for organizations. Enhance your cybersecurity strategy and prevent data breaches effectively.

Becoming a Graduate Pentester in London: A Path to a Rewarding Career in Cybersecurity
Oct 15, 2024 Information hub
Learn about the role of a graduate pentester London, the skills required, current trends, and how to thrive in this growing cybersecurity field. Discover your path to success today!
Penetration Tester Jobs: Your Guide to a Thriving Career in Cybersecurity
Oct 15, 2024 Information hub
Discover the world of penetration tester jobs, essential skills, and current trends in cybersecurity. Learn how to build a successful career in this high-demand field.
Explore the Growing Demand for Penetration Tester Jobs in the UK
Oct 15, 2024 Information hub
Learn about penetration tester jobs in the UK, including skills, responsibilities, and future trends. Explore why this role is crucial in today's cybersecurity landscape.

Understanding Penetration Testing Methodology: A Guide to Strengthening Cybersecurity
Oct 15, 2024 Information hub
Learn about penetration testing methodology, its steps, and importance in today’s cybersecurity landscape. Discover how it helps protect against threats and improve security.

Why a Security Test is Essential for Protecting Your Business
Oct 15, 2024 Information hub
Learn about the importance of a security test in today’s digital world. Explore different types of tests and how they help protect your systems and data from cyber threats effectively.
Essential Guide to Web App Pentest
Oct 15, 2024 Information hub
Find out how a web app pentest helps secure your online apps. Discover and fix weaknesses to protect your data and improve your overall security.
Understanding App Security: Why It Matters for Your Business
Oct 15, 2024 Information hub
Learn how app security is vital for protecting sensitive data, maintaining user trust, and preventing costly breaches. Discover common threats and effective solutions for safeguarding apps.

Enhancing Application Security: Best Practices and Future Trends
Oct 15, 2024 Information hub
Explore the significance of application security in today’s digital landscape. Learn about common threats, effective strategies, and future trends to enhance your application's safety and integrity.

Why Every Business Needs a DAST Scan: Protect Your Web Applications from Cyber Threats
Oct 15, 2024 Information hub
Explore the importance of a DAST scan in modern cybersecurity. Understand how it identifies vulnerabilities, protects web applications, and keeps your business safe from cyber threats.

Why DAST Testing is Essential for Securing Your Web Applications
Oct 15, 2024 Information hub
Discover the importance of DAST testing in identifying vulnerabilities in web applications. Ensure your organization's security and compliance with effective DAST testing strategies.

The Importance of DAST Tools for Web Security
Oct 15, 2024 Information hub
Discover how DAST tools improve your web security. They find weaknesses early to help prevent costly cyberattacks and keep you safe and compliant with rules.
Why Dynamic Application Security Testing is Important for Web Apps
Oct 15, 2024 Information hub
Understand why Dynamic Application Security Testing is crucial for web apps. It finds security problems, helping businesses defend against cyber threats and stay compliant.

How Dynamic Application Security Testing Tools Protect Your Applications
Oct 15, 2024 Information hub
Learn about Dynamic Application Security Testing tools and their importance in today’s cybersecurity landscape. They help find security issues early, protecting your applications from attacks.

Understanding SAST Scan: Enhancing Application Security in Development
Oct 15, 2024 Information hub
Discover the benefits of a sast scan for detecting vulnerabilities in applications. Improve security, save costs, and protect sensitive data effectively.

The Importance of SAST Testing: Building Secure Software from the Ground Up
Oct 15, 2024 Information hub
SAST testing analyzes source code to identify vulnerabilities before deployment. Learn its benefits, current trends, and how it secures software in today's digital landscape.

Understanding Static Application Security Testing: Key Benefits and Trends
Oct 15, 2024 Information hub
Discover how Static Application Security Testing (SAST) identifies vulnerabilities early in the development process, helping organizations enhance security and comply with regulations.

How to Check Website Safety for Free: Essential Tips for Online Security
Oct 15, 2024 Information hub
In today's digital age, website safety is crucial. Explore free tools and tips to check website safety, safeguard your personal information, and enjoy a secure online experience.

Why URL Scanners Are Essential for Cybersecurity in the Digital Age
Oct 15, 2024 Information hub
Learn how URL scanners work to identify harmful links, prevent phishing attacks, and safeguard your online presence, making them vital for individuals and businesses in today's digital world.

Essential Docker Security Best Practices for Protecting Your Containerized Applications
Oct 15, 2024 Information hub
Discover essential Docker Security Best Practices that help protect your containerized applications by using trusted images, setting resource limits, and managing permissions.
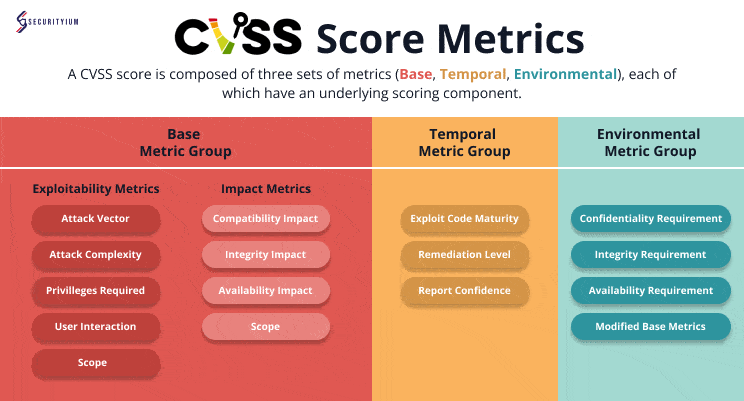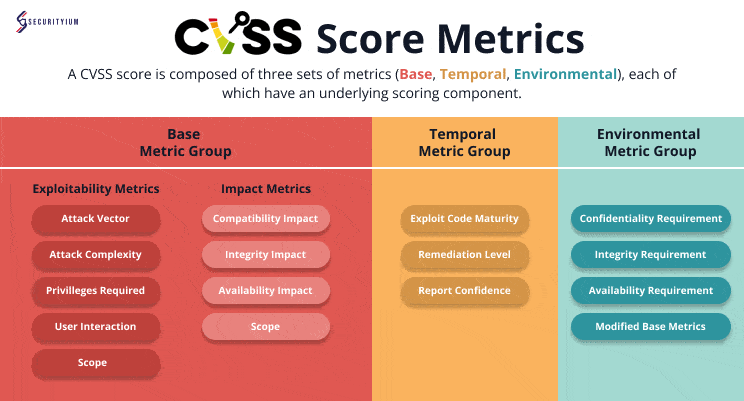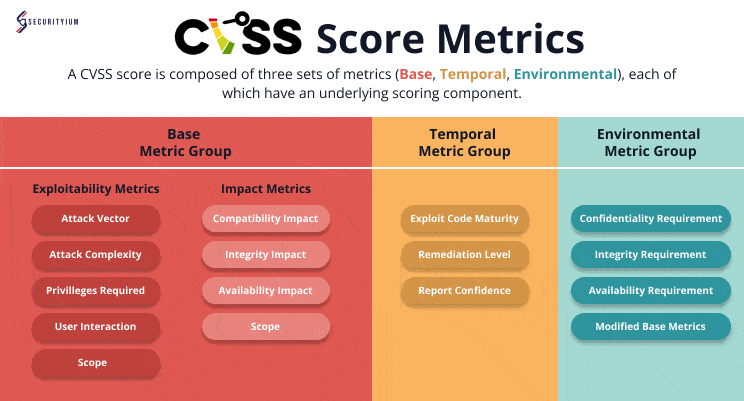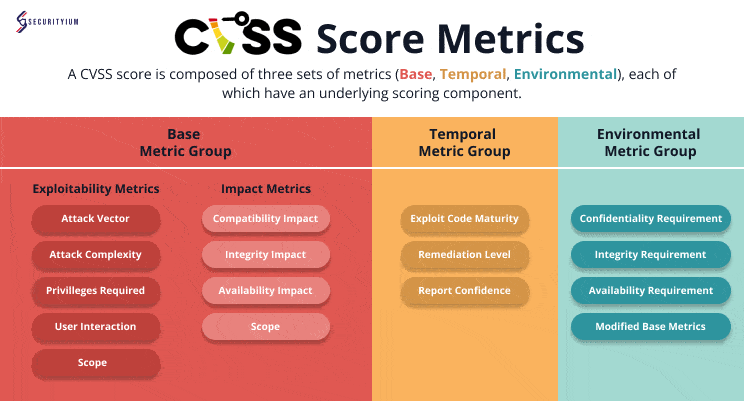
Understanding the Common Vulnerability Scoring System (CVSS): A Complete Guide
Oct 18, 2024 Information hub
Discover the Common Vulnerability Scoring System (CVSS), a framework for measuring and prioritizing security risks by scoring vulnerabilities from 0 to 10 for effective risk management.
How to Become a Pen Tester: Step-by-Step Guide for Aspiring Ethical Hackers
Oct 18, 2024 Information hub
Discover how to become a pen tester with a step-by-step guide on essential skills, certifications like CEH or OSCP, and hands-on experience to launch your career in ethical hacking.
How to Become a Penetration Tester: Step-by-Step Career Guide
Oct 18, 2024 Information hub
Discover how to become a penetration tester with a detailed guide covering key skills, certifications like CEH or OSCP, and hands-on experience to start a successful cybersecurity career.

How to Become a Pentester: A Complete Guide to Ethical Hacking
Oct 18, 2024 Information hub
Looking to learn how to become a pentester? Our guide covers the key steps, from mastering cybersecurity basics to obtaining certifications and gaining hands-on experience in ethical hacking.

Internal Penetration Testing: Protect Your Business from Insider Threats
Oct 18, 2024 Information hub
Internal penetration testing checks for security problems inside your business. Learn how it helps protect against insider threats and keeps your important data safe.

Understanding Internal Pentest: Safeguarding Against Insider Threats
Oct 18, 2024 Information hub
An internal pentest simulates insider attacks to identify security gaps within your organization. Discover its importance in today’s cybersecurity landscape.
Understanding Check Penetration Testing: A Crucial Step in Cybersecurity
Oct 18, 2024 Information hub
Check Penetration Testing is essential for businesses to identify vulnerabilities and enhance security. Learn its benefits, process, and why it should be part of your cybersecurity toolkit.

Understanding Computer Security Penetration Testing: A Key to Protecting Your Data
Oct 18, 2024 Information hub
Explore the importance of computer security penetration testing in today's digital landscape. Learn how it identifies weaknesses and enhances protection against cyber attacks.

The Importance of Cyber Security Penetration Testing: Protecting Your Data and Systems
Oct 18, 2024 Information hub
Explore the role of cyber security penetration testing in safeguarding sensitive data. Learn its benefits, types, and future trends in protecting organizations from evolving cyber threats.

Define Pentesting: Understanding Its Importance in Cybersecurity
Oct 18, 2024 Information hub
This guide will help you define pentesting, explore its significance in cybersecurity, and understand its methods, benefits, and current trends in protecting your digital assets.
Intrusion Testing: A Guide to Strengthening Cybersecurity and Preventing Cyberattacks
Oct 18, 2024 Information hub
Discover the importance of intrusion testing in protecting digital assets. Learn its methods, benefits, and how it can prevent costly cyberattacks before they happen.

IT Security Pen Testing: A Guide to Strengthening Your Cybersecurity Defenses
Oct 18, 2024 Information hub
Learn the importance of IT security pen testing to uncover system weaknesses, prevent breaches, and stay ahead of cyber threats in today's digital landscape.

Pen Test Web: Safeguarding Your Web Applications Against Cyber Threats
Oct 18, 2024 Information hub
Discover the importance of Pen Test Web for identifying security weaknesses in web applications and staying ahead of cyber threats. Improve security and comply with regulations.
Pen Test Website: Strengthen Your Security with Comprehensive Penetration Testing
Oct 18, 2024 Information hub
Discover how a pen test website can help protect your business by identifying security vulnerabilities and improving your defenses against potential cyberattacks. Stay safe online.

Pen Testing: The Ultimate Guide to Strengthen Your Cybersecurity
Oct 18, 2024 Information hub
Pen testing helps businesses find and fix vulnerabilities before cyberattacks occur. Learn its importance, types, and latest trends to safeguard your digital systems.

Pen Testing Meaning: Importance, Types, and Key Benefits in Cybersecurity
Oct 18, 2024 Information hub
Discover the pen testing meaning, its importance, and how it identifies security flaws. Learn the types of pen tests and why they are essential to your cybersecurity defense.

Pen Testing in UK: Importance, Trends, and Benefits for Organizations
Oct 18, 2024 Information hub
Discover why pen testing in UK is essential for identifying vulnerabilities, ensuring regulatory compliance, and enhancing security in an evolving cyber threat landscape.
Understanding Penetration Testing: A Key to Strengthening Cybersecurity
Oct 18, 2024 Information hub
Discover the importance of penetration testing in identifying vulnerabilities in your systems. Learn how it enhances security and helps you comply with regulations to safeguard your assets.

Mobile App Security Testing: Protect Your Apps from Cyber Threats
Oct 21, 2024 Information hub
Mobile app security testing is crucial for protecting user data, avoiding breaches, and ensuring compliance. Learn key methods and tools to secure your apps effectively.
Why Mobile Application Security Testing is Essential for Protecting Your Data
Oct 21, 2024 Information hub
Mobile application security testing is vital for safeguarding sensitive data, preventing cyberattacks, and complying with regulations. Learn key steps for ensuring app security.

What is Pentesting? A Complete Guide to Improving Cybersecurity
Oct 22, 2024 Information hub
Discover what is pentesting and how it helps find security vulnerabilities before attackers do. Learn its benefits, types, tools, and future trends for enhanced cybersecurity.
Black Box Penetration Testing: Identify and Prevent External Cyber Threats
Oct 22, 2024 Information hub
Black box penetration testing uncovers external vulnerabilities by simulating real-world cyberattacks. Learn its benefits, process, and how it enhances your security strategy.

Comprehensive Guide to White Box Penetration Testing for Better Cybersecurity
Oct 22, 2024 Information hub
Discover how white box penetration testing helps organizations find hidden vulnerabilities, improve system security, and protect against cyberattacks with full system access.

Comprehensive Methodology for Penetration Testing to Strengthen Cybersecurity
Oct 22, 2024 Information hub
Explore the methodology for penetration testing and how it helps find security flaws. Stay compliant, improve defenses, and protect your organization from cyberattacks.

Pentest Methodology: A Step-by-Step Approach to Effective Cybersecurity Testing
Oct 22, 2024 Information hub
Discover how a pentest methodology provides a structured way to find vulnerabilities, ensure cybersecurity, and comply with industry standards through detailed testing steps.

The Importance of a Penetration Testing Report for Stronger Cybersecurity
Oct 22, 2024 Information hub
A penetration testing report helps businesses find and fix cybersecurity risks. Discover how this report provides clear steps to protect systems from cyber threats.
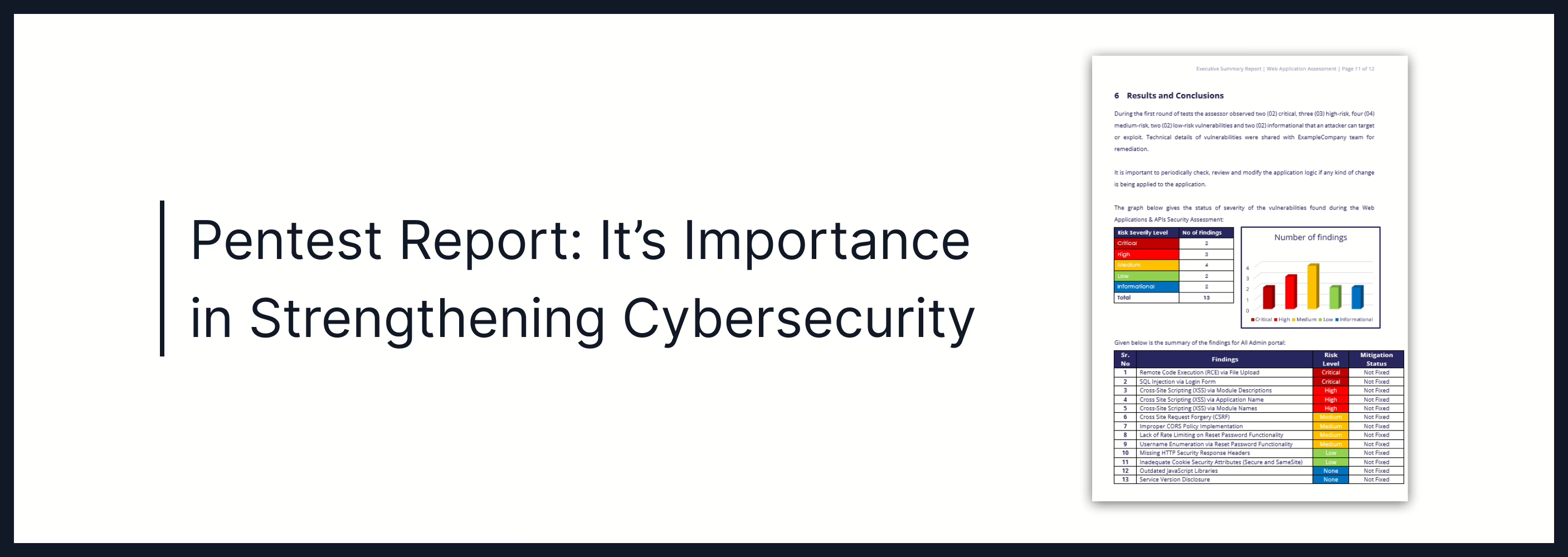
Pentest Report: It’s Importance in Strengthening Cybersecurity
Oct 22, 2024 Information hub
Discover how a pentest report outlines security risks and provides actionable steps to fix vulnerabilities. Learn how it strengthens cybersecurity and ensures compliance.

Black Box vs White Box Testing: Understanding the Differences and Best Practices
Oct 22, 2024 Information hub
Discover the essential differences between black box vs white box testing. Learn how to use each method effectively for secure, reliable, and high-quality software projects.

White Box and Black Box Testing: Understanding Key Differences and Benefits
Oct 22, 2024 Information hub
Discover how white box and black box testing work, their benefits, and why combining them helps you deliver secure, high-quality software in today's digital world.
Understanding White Box and Black Box Testing for Better Software Quality
Oct 22, 2024 Information hub
Discover the benefits of white box and black box testing in software development. Learn how both approaches help in improving functionality, security, and user experience.

Pen Test vs Vulnerability Scan: Understanding Their Roles in Cybersecurity
Oct 22, 2024 Information hub
Discover the key differences between pen test vs vulnerability scan. Learn how each method helps organizations identify vulnerabilities and enhance their cybersecurity defenses.
Penetration Testing vs Vulnerability Scanning: Understanding the Key Differences for Stronger Cybersecurity
Oct 22, 2024 Information hub
Explore penetration testing vs vulnerability scanning in this guide. Understand their differences, benefits, and how to combine them for a robust cybersecurity approach to protect your business.

Strengthening Cybersecurity with Vulnerability Assessment & Penetration Testing
Oct 22, 2024 Information hub
Learn how Vulnerability Assessment and Penetration Testing help organizations identify and fix security weaknesses to protect against cyber threats and ensure compliance.

The Essential Guide to Security Testing: Protect Your Digital Assets
Oct 22, 2024 Information hub
Learn about Security Testing and its role in identifying vulnerabilities. Explore methods, benefits, and current trends to enhance your organization's cybersecurity.

Enhance Your Security with a Comprehensive Web App Pen Test
Oct 22, 2024 Information hub
A web app pen test is essential for finding and fixing vulnerabilities in your applications. Learn why it's crucial for security, compliance, and protecting customer trust.

Essential Guide to Mobile App Security: Protecting Your Digital Assets
Oct 22, 2024 Information hub
Discover key trends and best practices in mobile app security. Learn how to protect sensitive data and mitigate risks in your mobile applications.

Essential Guide to Mobile Application Security
Oct 22, 2024 Information hub
Explore key challenges and best practices in Mobile application security. Learn how to safeguard your apps and protect sensitive user data effectively.

Why Mobile App Penetration Testing is Essential for Your App Security
Oct 22, 2024 Information hub
Mobile app penetration testing is crucial for finding security flaws in your app. Discover its importance, benefits, and how it safeguards user data against cyber threats.

Mobile App Pentesting: Essential Steps
Oct 22, 2024 Information hub
Mobile app pentesting helps find vulnerabilities in mobile applications. Discover its importance and key steps for securing your apps effectively.

Enhancing Security Through Mobile Application Penetration Testing
Oct 22, 2024 Information hub
Mobile application penetration testing helps find security flaws in apps before hackers exploit them. Discover its importance, trends, and benefits for a secure mobile experience.

Unlock Your Future with Cyber Security Courses in London: A Comprehensive Guide
Oct 22, 2024 Information hub
Explore the best cyber security courses in London. Learn essential skills, gain hands-on experience, and network with industry experts to advance your career in this critical field.

Discover the Importance of Cyber Security Exhibitions in Today’s Digital Age
Oct 22, 2024 Information hub
Learn how cyber security exhibitions are vital for showcasing new technologies, networking opportunities, and education in the ever-evolving landscape of cyber threats and solutions.

Understanding Penetration Hacking: Essential Strategies for Cybersecurity
Oct 22, 2024 Information hub
Explore penetration hacking and its role in cybersecurity. Discover types, benefits, and trends to enhance your organization's defenses against cyber threats.

Why Every Organization Needs a Penetration Tester for Strong Cybersecurity
Oct 22, 2024 Information hub
Discover the vital role of a penetration tester in today’s digital landscape. Explore their importance, types, and how they help organizations improve security and compliance.

The Essential Role of Security and Penetration Testing in Cybersecurity
Oct 22, 2024 Information hub
Learn about the importance of security and penetration testing in identifying vulnerabilities, preventing data breaches, and enhancing your organization's cybersecurity strategy.

Understanding the Importance of Security Testing and Penetration Testing in Today’s Cybersecurity Landscape
Oct 22, 2024 Information hub
Learn the significance of security testing and penetration testing in today’s digital world. Discover how these methods help identify vulnerabilities and improve your organization's defenses.

Enhance Your Security with Website Penetration Testing: A Comprehensive Guide
Oct 22, 2024 Information hub
Website penetration testing helps identify vulnerabilities in your site by simulating attacks. Learn its importance, types, process, and how it enhances security against cyber threats.

Top 10 Best Practices for Mobile Application Pentesting
Oct 22, 2024 Information hub
Discover the top best practices for mobile application pentesting, including testing methods, security tips, and tools to protect your mobile apps against potential cyber threats.

Comprehensive Guide to Web App Penetration Testing: Secure Your Applications from Cyber Threats
Oct 22, 2024 Information hub
Discover the importance of web app penetration testing, a proactive method to find vulnerabilities and protect web applications from potential cyberattacks and data breaches.
Why Network Pentesting is Critical for Your Cybersecurity Strategy
Oct 22, 2024 Information hub
Network pentesting helps identify and fix security gaps before hackers exploit them. Explore how this proactive approach strengthens your defenses against cyberattacks.
Certified Penetration Tester Certification
Oct 22, 2024 Information hub
Discover the importance of the Certified Penetration Tester Certification and how it can help professionals enhance cybersecurity skills and protect systems from cyber threats.

Licensed Penetration Tester: Role, Importance, and How to Become One
Oct 22, 2024 Information hub
Discover the role and benefits of a licensed penetration tester. Explore how to become one and their importance in safeguarding against cyber threats in today's world.

Pen Testing Certification: Boost Your Cybersecurity Career
Oct 22, 2024 Information hub
Discover why getting a pen testing certification is key to advancing your cybersecurity career and helping organizations protect their systems from cyber threats.

Penetration Testing Certification: Boost Your Cybersecurity Skills and Career
Oct 22, 2024 Information hub
Explore how penetration testing certification helps validate your skills in ethical hacking, enhances credibility, and opens up new job opportunities in the growing cybersecurity field.

Automated Pen Testing: A Fast and Efficient Way to Secure Your Digital Assets
Oct 22, 2024 Information hub
Automated pen testing provides a fast, scalable way to identify vulnerabilities and protect digital systems. Discover how automation enhances security, reduces costs, and ensures continuous testing.
The Benefits of Cyber Security Certification for Career Growth and Job Security
Oct 23, 2024 Information hub
Cyber security certification proves your skills and expertise in the field, offering career growth and job security. Explore certifications and stay ahead in the cybersecurity industry.
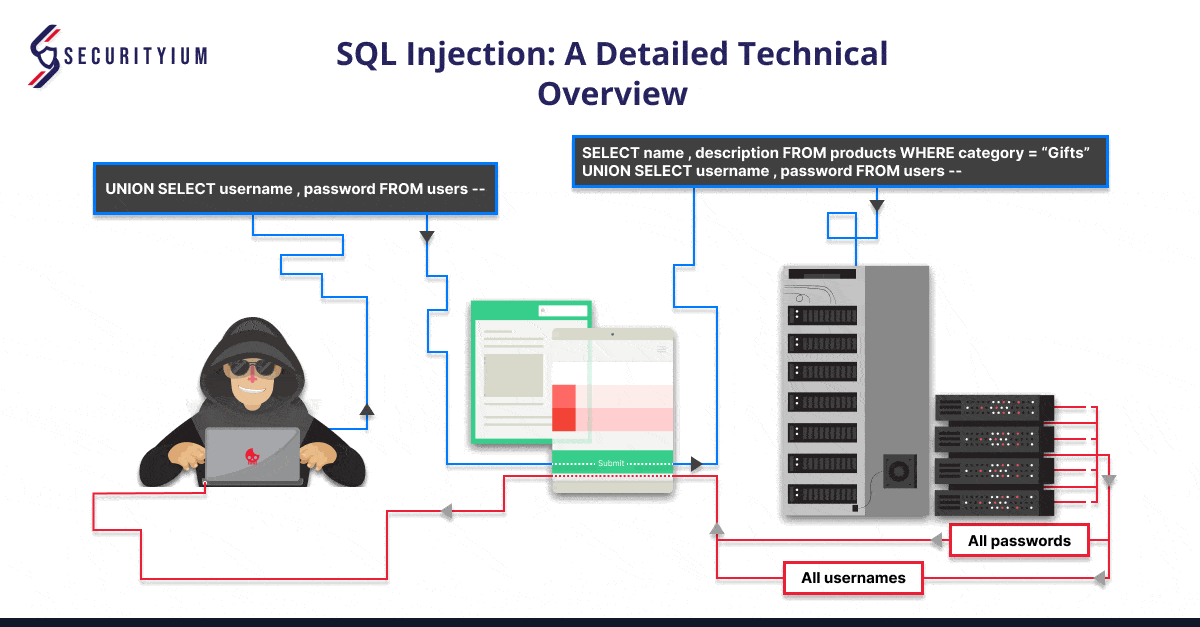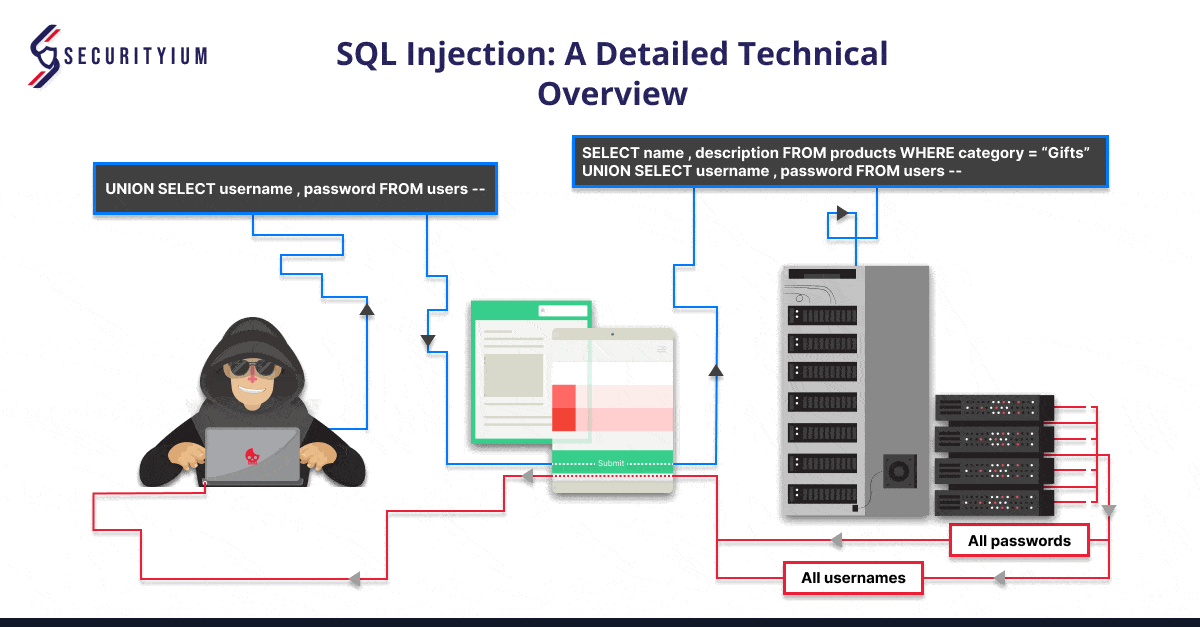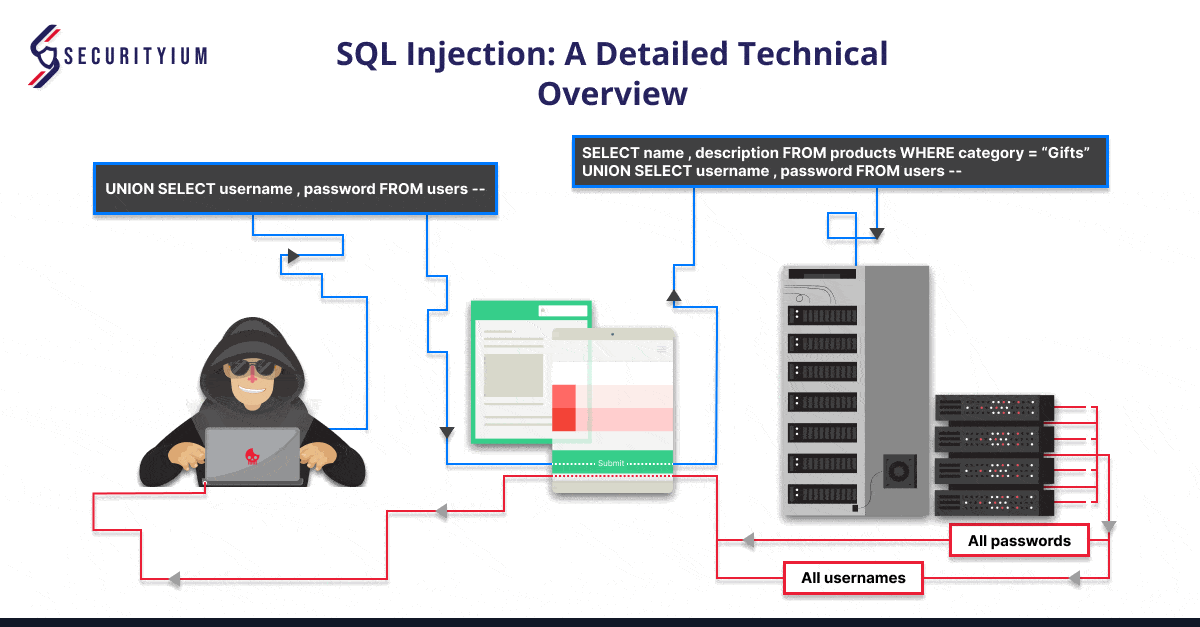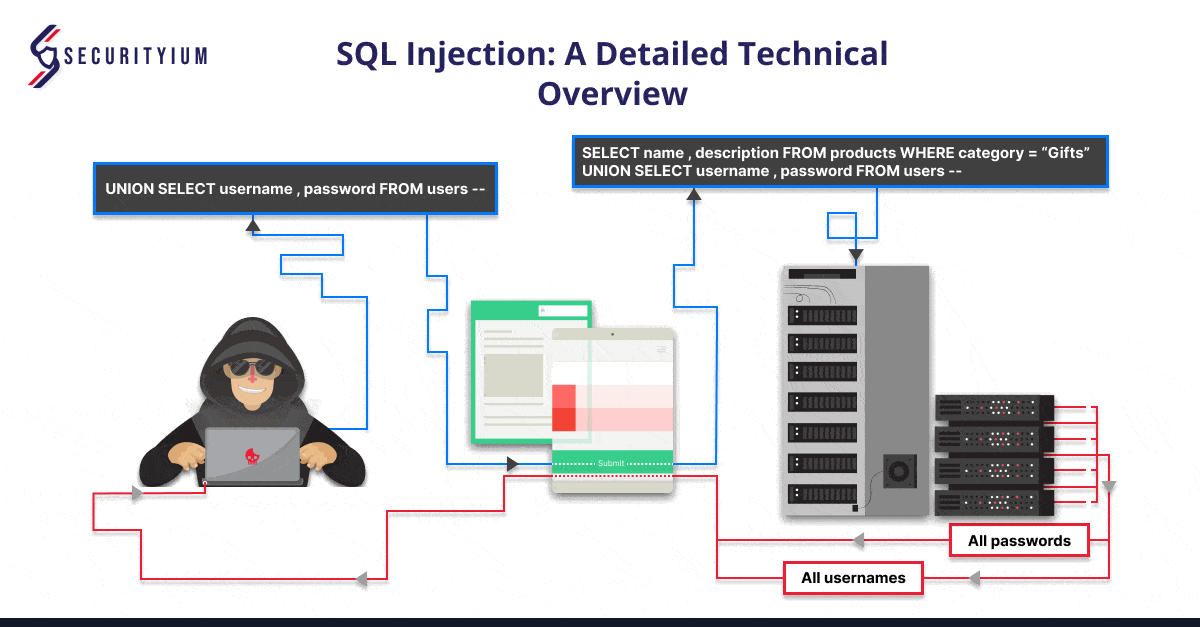
SQL Injection: A Detailed Technical Overview
Oct 25, 2024 Technical Write ups
Learn about SQL Injection, its types, real-world cases, and steps to prevent it. Secure your web applications from data breaches and unauthorized access.

API Security: Key Threats, Best Practices, and Real-World Examples
Oct 25, 2024 Information hub
Discover the essentials of API security, including threats, best practices like strong authentication, rate limiting, and encryption to safeguard your APIs.

API Authentication: Securing API Access
Oct 25, 2024 Information hub
Learn about API authentication, why it’s essential, and which methods best secure API access. Discover trends like Zero Trust and passwordless security for enhanced protection and compliance.

Essential API Authentication Methods for Secure Data Access in 2025
Oct 25, 2024 Information hub
Learn about API authentication methods that protect data access, from simple API keys to advanced OAuth 2.0. Discover their pros, cons, and trends shaping API security in the digital world.

Essential API Security Best Practices to Safeguard Your Data
Oct 25, 2024 Information hub
Discover API security best practices to shield data from threats. Learn practical strategies like strong authentication, encryption, and monitoring to secure your APIs.
Why Application Programming Interface Security is Crucial?
Oct 25, 2024 Information hub
Explore why application programming interface security matters, the latest security challenges, and best practices to protect APIs from cyberattacks and ensure data safety.

Essential Guide to OWASP Top 10
Oct 25, 2024 Information hub
Understand the OWASP Top 10 risks to web apps and how to secure against them. Discover the latest threats, compliance needs, and strategies to boost your web app security.

Understanding the Open Web Application Security Project (OWASP) Top Ten for Web App Security
Oct 25, 2024 Technical Write ups
Learn about the Open Web Application Security Project (OWASP) Top Ten, a key guide for tackling the most critical web app vulnerabilities. Follow best practices to reduce security risks and ensure data protection.

Top 12 Best Practices for Effective Web Application Pentesting
Oct 29, 2024 Information hub
Discover the top 12 best practices for web application pentesting to strengthen security, identify vulnerabilities, and protect your app from cyberattacks.

15 Best Practices for Successful Network Penetration Testing
Nov 5, 2024 Information hub
Explore 15 essential network penetration testing practices to identify and fix vulnerabilities, strengthen defenses, and protect your network from cyber threats.

The Importance of Application Security Testing
Nov 5, 2024 Information hub
Discover the importance of application security testing to secure data, avoid breaches, and comply with regulations. Learn key testing types and emerging trends.

Essential Security Testing Tools for Identifying and Reducing Cyber Risks
Nov 5, 2024 Information hub
Explore various security testing tools like SAST, DAST, and IAST, and learn how they help identify cyber risks, enhance compliance, and strengthen cybersecurity defenses.

Best Mobile Application Penetration Testing Tools in 2025
Nov 5, 2024 Information hub
Learn about essential mobile application penetration testing tools, their features, and best practices to secure your app, protect user data, and stay compliant with regulations.
SAST Meaning: Secure Your Code with Static Security Testing
Nov 5, 2024 Information hub
Discover the meaning of SAST, a method for finding security issues in code early in development. See why SAST is key for catching vulnerabilities, enhancing code quality, and ensuring compliance.

What is SAST: A Guide to Secure Your Applications
Nov 5, 2024 Information hub
Discover what SAST is and its role in securing code from vulnerabilities. Our guide covers benefits, real-world examples, and integration tips for effective app security.

Master Code Analyse: Boost Software Quality and Security
Nov 5, 2024 Information hub
Discover the impact of code analyse on software development. From enhancing code quality and security to reducing technical debt, this guide covers practical examples and trends.
Understanding Code Analysis for Better Software Quality
Nov 5, 2024 Information hub
Explore the role of code analysis in software development. Discover its types, benefits, and tools to enhance code quality and security.

Code Analysis Tools: Enhancing Software Quality and Security
Nov 5, 2024 Information hub
Learn the importance of code analysis tools in software development. Explore their types, benefits, and how they help improve code quality and security.
Static Code Analyzers: Boost Code Quality & Security Fast
Nov 6, 2024 Information hub
Learn the importance of static code analyzers in software development. Explore their benefits, like early bug detection and better code security, for quality-driven projects.

Boost Software Quality with Static Code Tools in Development
Nov 6, 2024 Information hub
Learn how static code tools identify coding issues, enforce standards, and boost security in software development, helping teams save time and deliver high-quality code.

Static Program Analysis: Improve Code Quality & Security
Nov 6, 2024 Information hub
Discover the benefits of static program analysis for better software. Learn how it detects bugs and security issues early, saving time, cost, and boosting code quality.

Why Static Program Analysis Tools Matter for Code Quality
Nov 6, 2024 Information hub
Learn why static program analysis tools are essential for code quality, security, and efficiency. Discover their benefits, features, and latest trends to streamline software development.

Static Source Code Analysis: Boost Software Quality & Security
Nov 6, 2024 Information hub
Static source code analysis identifies vulnerabilities and improves code quality by detecting bugs early. Discover the key benefits, trends, and practical examples for secure and maintainable software.
What is Static Code? Boost Quality & Security in Software
Nov 6, 2024 Information hub
Discover what static code is, its importance for secure, high-quality software, and how integrating static code analysis can enhance efficiency and security in development.

What is Static Code Analysis: Boosting Code Quality & Security
Nov 6, 2024 Information hub
Learn what static code analysis is, why it's essential for boosting code quality, reducing bugs, and enhancing security in development. Explore benefits, tools, and future trends to optimize your software process.

Why SQL Vulnerability Test is Essential for Data Security?
Nov 6, 2024 Information hub
An SQL vulnerability test detects weaknesses in databases to prevent cyberattacks and data breaches. Learn how it helps organizations stay secure, compliant, and build customer trust.
Understanding Test Injection SQL: Protect Your Database
Nov 6, 2024 Information hub
Discover the risks of SQL injection, a major threat to databases today. Learn how attacks work and get essential tips on preventing SQL injection for stronger database security.
OWASP Web Top 10: Key Risks for Securing Web Apps
Nov 6, 2024 Information hub
Learn about the OWASP Web Top 10, a list of key web security risks. Discover how to secure web applications with examples, solutions, and preventive tips.
What is OWASP? A Guide to Web Application Security
Nov 6, 2024 Information hub
Discover OWASP, a key resource in web security. This guide covers OWASP's mission, the Top 10 risks, tools like ZAP, and trends in application security.
Understanding CERT Information Security
Nov 6, 2024 Information hub
Explore CERT Information Security's role in managing and preventing cyber threats. From incident response to threat intelligence, discover how CERTs keep systems safe.

Open Source Vulnerability Scanner for Stronger Security
Nov 6, 2024 Information hub
Learn how open source vulnerability scanners help detect security risks. From features to benefits, find out how these tools strengthen cybersecurity in any business.

Essential Pen Testing Software for Cybersecurity
Nov 6, 2024 Information hub
Pen testing software automates vulnerability detection, securing systems against cyber threats. Learn its types, benefits, and latest trends to boost your cybersecurity.
Protect Your Business with Automated Scanning Tools
Nov 6, 2024 Information hub
Automated scanning tools help businesses of all sizes stay secure by identifying vulnerabilities, ensuring compliance, and offering real-time monitoring, learn why they're essential.

Top Web Application Penetration Testing Tools for 2025
Nov 6, 2024 Information hub
Explore essential web app penetration testing tools like Burp Suite, OWASP ZAP, and Nmap. Understand how these tools help identify vulnerabilities, improve security, and safeguard sensitive data.

Why Website Pen Testing is Crucial for Cybersecurity
Nov 6, 2024 Information hub
Website pen testing helps identify and fix vulnerabilities to prevent cyberattacks. Learn how this proactive approach safeguards your website and sensitive data.

Black Box Testing vs White Box Testing: Key Differences
Nov 6, 2024 Information hub
Explore the differences between Black Box Testing and White Box Testing, their uses, challenges, and how both enhance software quality and security.

Black Box Testing: Essential for Quality Software Assurance
Nov 6, 2024 Information hub
Black Box Testing helps identify issues in software by focusing on functionality, user experience, and performance without needing code knowledge.
Black Box Testing and Grey Box Testing: Key Differences
Nov 6, 2024 Information hub
Explore black box testing and grey box testing, their key features, types, benefits, and how they improve software functionality and security.

Black Box Testing and White Box Testing: Key Differences
Nov 6, 2024 Information hub
Explore black box testing and white box testing, their differences, types, benefits, and how both play a role in ensuring high-quality software.
Understanding Black Box Testing in Software Testing
Nov 6, 2024 Information hub
Explore black box testing in software testing, its importance, types, techniques, and benefits for creating high-quality, user-friendly software products.
Understanding Black Box Testing Software for Quality
Nov 6, 2024 Information hub
Explore black box testing software to ensure software functionality meets user expectations, enhance UX, and streamline quality assurance in development

Black Box, White Box Testing: Key Differences and Benefits
Nov 6, 2024 Information hub
Explore black box white box testing, their key differences, and how these methods ensure robust, secure, and high-performing software in development.

Blackbox Testing and Whitebox Testing: Key Differences
Nov 6, 2024 Information hub
Understand blackbox testing and whitebox testing, their advantages, challenges, and how both can improve your software quality and security.
Blackbox vs Whitebox Testing: Key Differences & Benefits
Nov 6, 2024 Information hub
Discover blackbox vs whitebox testing, their differences, benefits, and how combining both improves software quality and security.

White and Black Box Testing: Key Techniques & Benefits
Nov 6, 2024 Information hub
Explore white and black box testing, their roles in software quality, key techniques, and how they contribute to a robust testing process.

Gray Box Testing: Enhance Software Quality and Security
Nov 6, 2024 Information hub
Learn how gray box testing combines insights from both black and white box testing to enhance software quality, detect bugs faster, and improve security in complex applications.

Grey Box Testing: Enhance Security and Test Coverage
Nov 7, 2024 Information hub
Learn how grey box testing combines the best of black and white box testing to enhance security, boost test coverage, and streamline testing in agile development.

Grey Box Testing in Software Testing: Boost Quality and Security
Nov 7, 2024 Information hub
Grey box testing in software testing combines black and white box testing techniques to ensure quality, find vulnerabilities, and increase software test coverage.

Cyber Security Pen Testing: Strengthen Your Defense
Nov 7, 2024 Information hub
Cyber security pen testing simulates attacks to identify weaknesses in systems, helping organizations strengthen their defenses and stay ahead of evolving cyber threats.
Understanding Security Pen Testing for Stronger Cyber Defense
Nov 7, 2024 Information hub
Security pen testing reveals vulnerabilities in systems, apps, and networks, helping organizations prevent cyber threats and protect sensitive data effectively.

The Ultimate Guide to Security Penetration Testing
Nov 7, 2024 Information hub
Explore security penetration testing, its benefits, and how it can safeguard your systems. This guide covers key methods, challenges, and top trends in cyber defense.

What Is a Pen Tester? Role and Importance in Cybersecurity
Nov 7, 2024 Information hub
Learn what a pen tester is and their crucial role in cybersecurity. Find out how they detect security risks, prevent breaches, and improve system protection.
Strengthen Security with White Box Pen Testing Explained
Nov 7, 2024 Information hub
White box pen testing dives deep into system code and design to find security weaknesses. This proactive testing helps stop cyber threats before they can harm your system.

Understanding What Is White Testing: Methods and Importance
Nov 7, 2024 Information hub
Discover what white testing is and why it’s vital for code quality, security, and regulatory compliance. Learn about key methods, trends, and actionable steps.
Mastering the White Box Technique for Better Software Testing
Nov 7, 2024 Information hub
Explore the white box technique in software testing, its key features, benefits, trends, and future developments to improve code quality, security, and performance.

White Box Testing: Enhancing Software Quality and Security
Nov 7, 2024 Information hub
White box testing improves software quality by identifying bugs, optimizing performance, and ensuring security. Discover its benefits and applications for better software.

Benefits of White Box Testing in Software Testing
Nov 7, 2024 Information hub
Explore the key benefits and techniques of white box testing in software testing to enhance code quality, security, and ensure comprehensive test coverage.
White Box Testing Software: Key Benefits and Trends
Nov 7, 2024 Information hub
Learn how white box testing software helps improve code quality, security, and efficiency by identifying issues early in the development process.

Essential Guide to Whitebox Testing for Quality Software
Nov 7, 2024 Information hub
Discover the importance of whitebox testing in software development, its techniques, benefits, and how it enhances code quality, security, and efficiency.

Guide to Vulnerability Assessment Types and Methodology
Nov 7, 2024 Information hub
Learn about vulnerability assessment types and methodology to secure IT infrastructure. Understand network, host, application, and database assessments to boost cybersecurity.

Vulnerability Assessment Framework: Key Steps & Benefits
Nov 7, 2024 Information hub
Understand how a vulnerability assessment framework identifies and addresses security risks, ensuring proactive risk management and robust data protection.

Essential Security Tools for Protecting Your Data Online
Nov 7, 2024 Information hub
Discover the importance of essential security tools in protecting sensitive data and preventing cyber threats. Learn practical strategies to secure your network, cloud, and devices.
Boost Website Health and Security with a Webpage Scanner
Nov 7, 2024 Information hub
A webpage scanner helps keep your site secure, optimized, and compliant. Learn how this tool detects vulnerabilities, boosts SEO, and enhances user experience.

Managed Vulnerability: Proactive Security Against Cyber Threats
Nov 7, 2024 Information hub
Explore managed vulnerability services and discover how they help companies identify, assess, and reduce security risks through continuous monitoring and expert support.
Effective Threat and Vulnerability Management for Cybersecurity
Nov 7, 2024 Information hub
Learn about threat and vulnerability management and its role in preventing cyber threats. Discover key strategies, benefits, and trends to protect your business.

Vuln Management: Essential for Cybersecurity in 2025
Nov 7, 2024 Information hub
Vuln management is crucial in cybersecurity, helping businesses reduce risks, enhance security, and stay compliant. Learn how effective vulnerability management builds a solid defense against cyber threats.

Essential Steps for a Strong Vulnerability Management Procedure
Nov 7, 2024 Information hub
A vulnerability management procedure is key for securing your systems. Discover steps to identify, prioritize, and fix vulnerabilities, protecting your organization from cyber threats.

Effective Vulnerability Management Process for Stronger Security
Nov 7, 2024 Information hub
Explore the vulnerability management process, a step-by-step approach to find, evaluate, and address security risks, helping organizations strengthen their defenses.

Effective Vulnerability Management Program for Cyber Defense
Nov 7, 2024 Information hub
Discover how a vulnerability management program helps prevent cyber risks by identifying and fixing system weaknesses. Explore essential steps, trends, and solutions to stay secure.

Essential Guide to Net Scanners for Modern Network Security
Nov 7, 2024 Information hub
Discover how a net scanner helps IT teams secure networks by mapping devices, detecting vulnerabilities, and managing network performance for safety and efficiency.

Essential Guide to Network Scanners for Stronger Security
Nov 7, 2024 Information hub
Discover how network scanners help secure IT networks by identifying vulnerabilities, monitoring devices, and ensuring compliance. Learn the latest trends and benefits.

CERT-In: India’s Cybersecurity Shield Against Digital Threats
Nov 8, 2024 Information hub
Learn how CERT-In protects India's digital space by responding to cyber threats, promoting best practices, and fostering collaboration for a safer cyberspace.

Indian Computer Emergency Response Team Role in Cybersecurity
Nov 8, 2024 Information hub
Explore how the Indian Computer Emergency Response Team (CERT-In) responds to cyber threats, raises cybersecurity awareness, and collaborates globally to protect India's digital landscape.

Benefits of CERT-IN Certification for Cybersecurity
Nov 8, 2024 Information hub
Learn how CERT-IN certification boosts cybersecurity, builds customer trust, and ensures regulatory compliance, helping organizations stay secure and competitive.

Role of a CERT Empaneled Security Auditor in Cyber Defense
Nov 8, 2024 Information hub
Learn how a CERT Empaneled Security Auditor helps organizations secure digital assets, ensure regulatory compliance, and address cybersecurity risks effectively.

CERT-IN Certification: Strengthen Cybersecurity for Your Business
Nov 8, 2024 Information hub
Discover the benefits of CERT-IN Certification for businesses, including better cybersecurity, regulatory compliance, and increased customer trust in today's digital world.

Essential Steps in the CERT-IN Certification Process
Nov 8, 2024 Information hub
Explore the CERT-IN Certification Process to help businesses comply with cybersecurity standards, enhance data protection, and establish client confidence.
CERT-IN Cyber Incident Reporting Guidelines: A Complete Guide
Nov 8, 2024 Information hub
Explore CERT-IN Cyber Incident Reporting Guidelines, covering key steps to report incidents, stay compliant, and build a strong cybersecurity defense.
CERT-In Cyber Security: Safeguarding India’s Digital Landscape
Nov 8, 2024 Information hub
Learn how CERT-In cyber security helps protect India's digital infrastructure by responding to incidents, issuing alerts, and fostering public awareness to combat cyber threats.

Cyber Essentials Certification: A Guide to Secure Your Business
Nov 8, 2024 Information hub
Understand Cyber Essentials certification, its importance, the two levels, and how it strengthens your business’s cybersecurity against common threats.

Understanding CERT-IN Directions for Cybersecurity in India
Nov 8, 2024 Information hub
Explore the significance of CERT-IN Directions in India and how organizations can enhance their cybersecurity by following these essential guidelines.
Full Form of CERT-In: Role & Importance in Cybersecurity
Nov 8, 2024 Information hub
Explore the full form of CERT-In, its functions, and how it strengthens India's cybersecurity efforts to prevent and mitigate cyber threats.

Understanding CERT-IN Guidelines for Enhanced Cybersecurity
Nov 8, 2024 Information hub
Learn about CERT-IN Guidelines to strengthen cybersecurity, enhance incident response, and protect digital assets in India.

Why CERT-In Security Audit is Essential for Your Business
Nov 8, 2024
A CERT-In Security Audit helps identify vulnerabilities, improve security, ensure compliance, and protect your organization from cyber threats.

Understanding the CERT-IN VAPT Report: Key Insights
Nov 8, 2024 Information hub
Explore the CERT-IN VAPT report, its components, and how it helps organizations identify vulnerabilities and enhance their cybersecurity defenses.

Understanding the Importance of CERT-In for Cybersecurity
Nov 8, 2024 Information hub
Explore the importance of CERT-In in protecting critical infrastructure, responding to cyber incidents, and fostering cybersecurity collaboration across India.

Responsibilities of CERT-In: Key Roles in Cybersecurity
Nov 8, 2024
Learn about the responsibilities of CERT-In in India, including cybersecurity incident response, threat intelligence sharing, and raising awareness.

What is CERT-In and How It Enhances Cybersecurity
Nov 8, 2024 Information hub
Discover what CERT-In is and how it helps safeguard India’s cyberspace by responding to incidents and raising cybersecurity awareness.

Complete Guide to Android Pentesting: Tools and Techniques
Nov 8, 2024 Information hub
This guide covers Android pentesting essentials, including lab setup, APK analysis, SSL pinning bypass techniques, and tools like MobSF, ADB, and Burp Suite for securing Android applications.

Effective Strategies to Reduce Attack Surface in 2025
Nov 11, 2024 Information hub
Learn key methods to reduce your attack surface, including vulnerability assessments, strong access controls, and employee training for better cybersecurity.

Understanding What is Attack Surface in Cybersecurity
Nov 11, 2024 Information hub
Discover what is attack surface in cybersecurity, explore key types, and find effective strategies to reduce vulnerabilities and secure your organization.

Types of Attack Surface in Cybersecurity: A Complete Guide
Nov 11, 2024 Information hub
Learn about types of attack surface in cybersecurity and how to secure each type with effective strategies, real-world examples, and practical tips.

Comprehensive Guide to Attack Surface Management
Nov 11, 2024 Information hub
Explore attack surface management, covering its importance, practical examples, current trends, and actionable strategies to secure your digital ecosystem effectively.

Comprehensive Guide to Attack Surface Scanning
Nov 11, 2024 Information hub
Explore the essentials of attack surface scanning to secure your organization from cyber threats. Understand its relevance, benefits, and modern trends in cybersecurity.

Effective Strategies for Attack Surface Reduction
Nov 11, 2024 Information hub
Explore key methods for attack surface reduction, from network and endpoint security to zero-trust models. Protect your organization by minimizing cyber vulnerabilities.

ASR Rules: Key to Blocking Cyber Threats & Enhancing Security
Nov 11, 2024 Information hub
Discover how ASR rules can protect your organization by blocking risky activities, preventing credential theft, and securing endpoints for robust digital defenses.
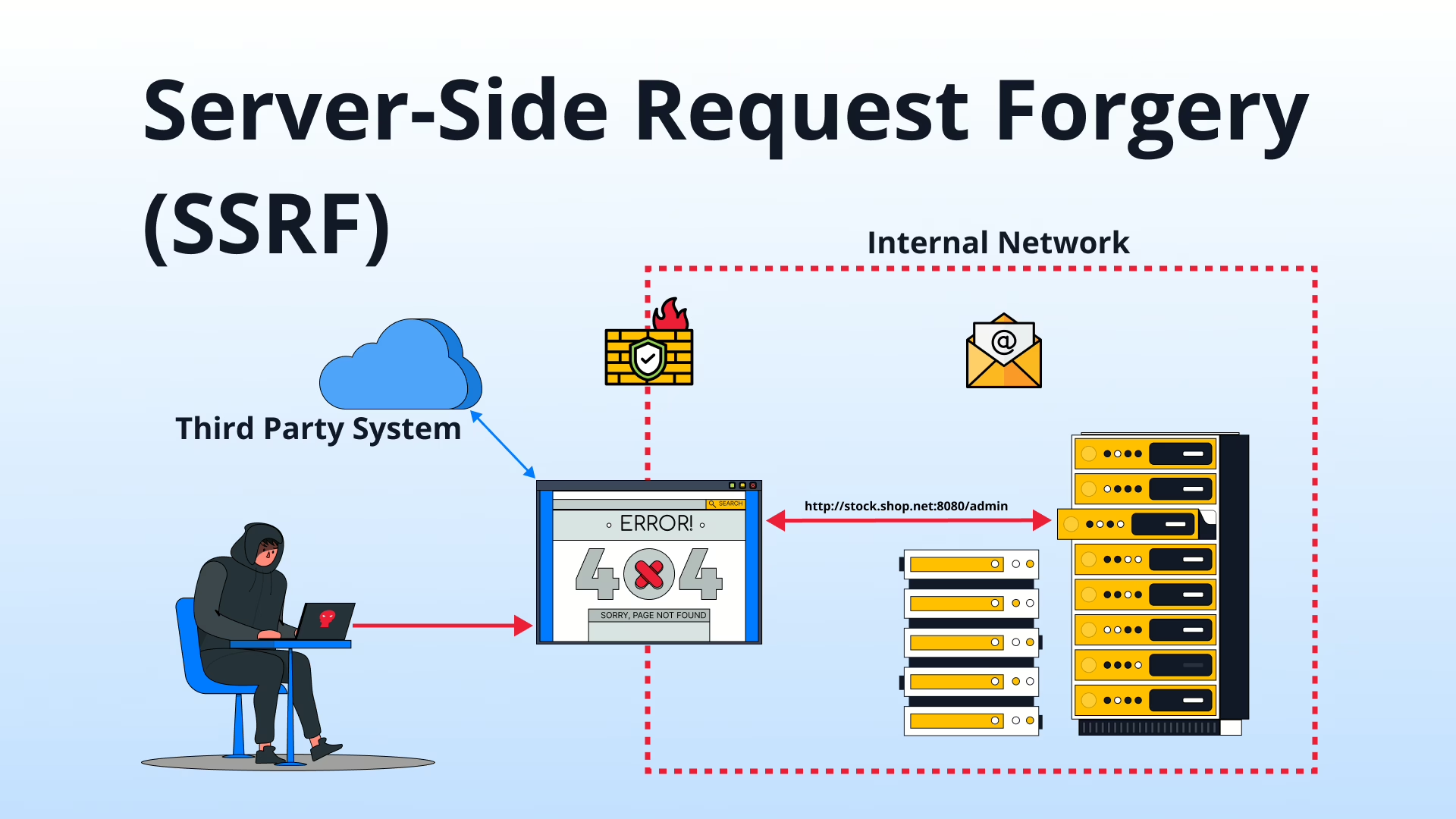
Server-Side Request Forgery (SSRF): Threats and Mitigation
Nov 15, 2024 Technical Write ups
Server-Side Request Forgery (SSRF) is a critical vulnerability that attackers exploit to access sensitive data. Discover its risks, real-world examples, and effective mitigation strategies.

Cloud Data Security Best Practices: Comprehensive Guide
Nov 19, 2024 Information hub
Discover cloud data security best practices to secure your business's sensitive information against unauthorized access and cyber threats.
Vulnerability Tracking Using OCRC: A Structured Framework for Effective Penetration Testing
Nov 21, 2024 Information hub
Discover how the OCRC framework enhances vulnerability tracking in penetration testing with clear stages—Open, Confirmed, Resolved, and Closed.

What Is Vulnerability Assessment and How Is It Conducted?
Nov 22, 2024 Information hub
Discover the importance of vulnerability assessments in identifying security risks and protecting your systems from potential attacks. Learn how it's done and why it matters.
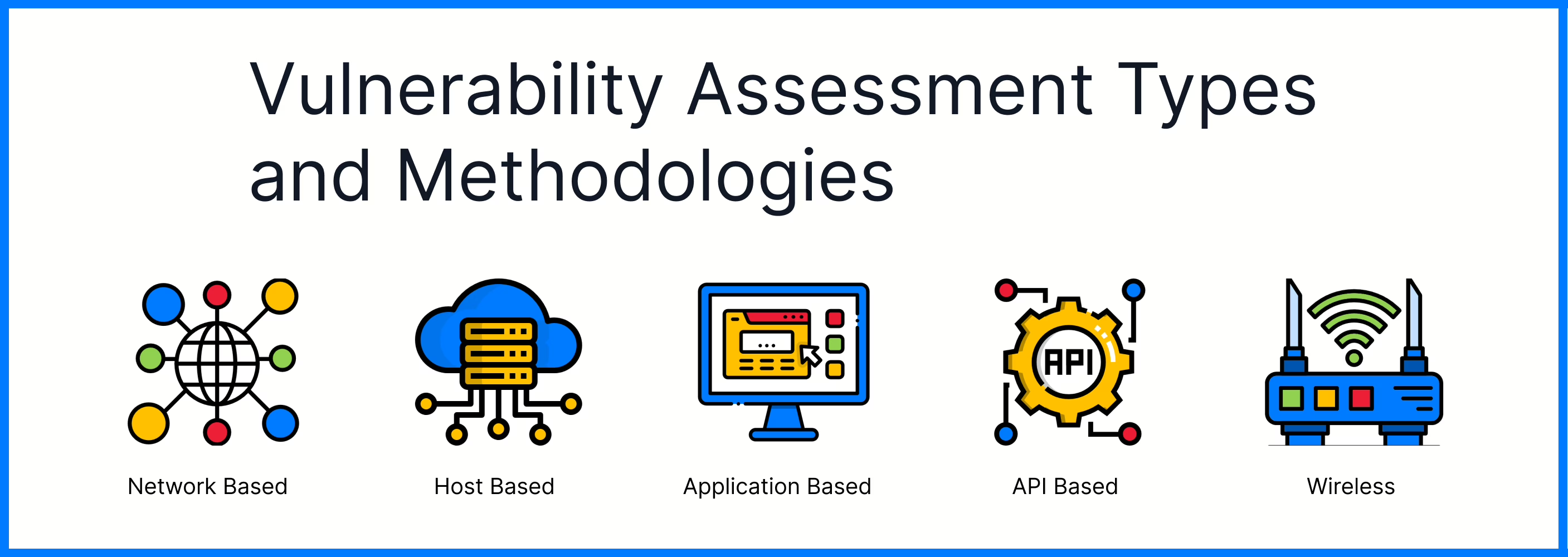
Vulnerability Assessment Types & Methodologies Explained
Nov 22, 2024 Information hub
Explore various vulnerability assessment types & methodologies to safeguard your network, systems, and applications from potential security threats.

Comparing Vulnerability Management Frameworks: CISA, NIST & SANS
Nov 26, 2024 Information hub
Explore vulnerability management frameworks like CISA, NIST, and SANS. Learn tools and strategies to identify, assess, and fix vulnerabilities effectively.

A Quick Note For AWS Penetration Testing: Securing Your Cloud Infrastructure
Nov 26, 2024 Information hub
Discover AWS penetration testing and its importance in identifying vulnerabilities in cloud environments. Learn methods, tools, and best practices to ensure data and workload security.
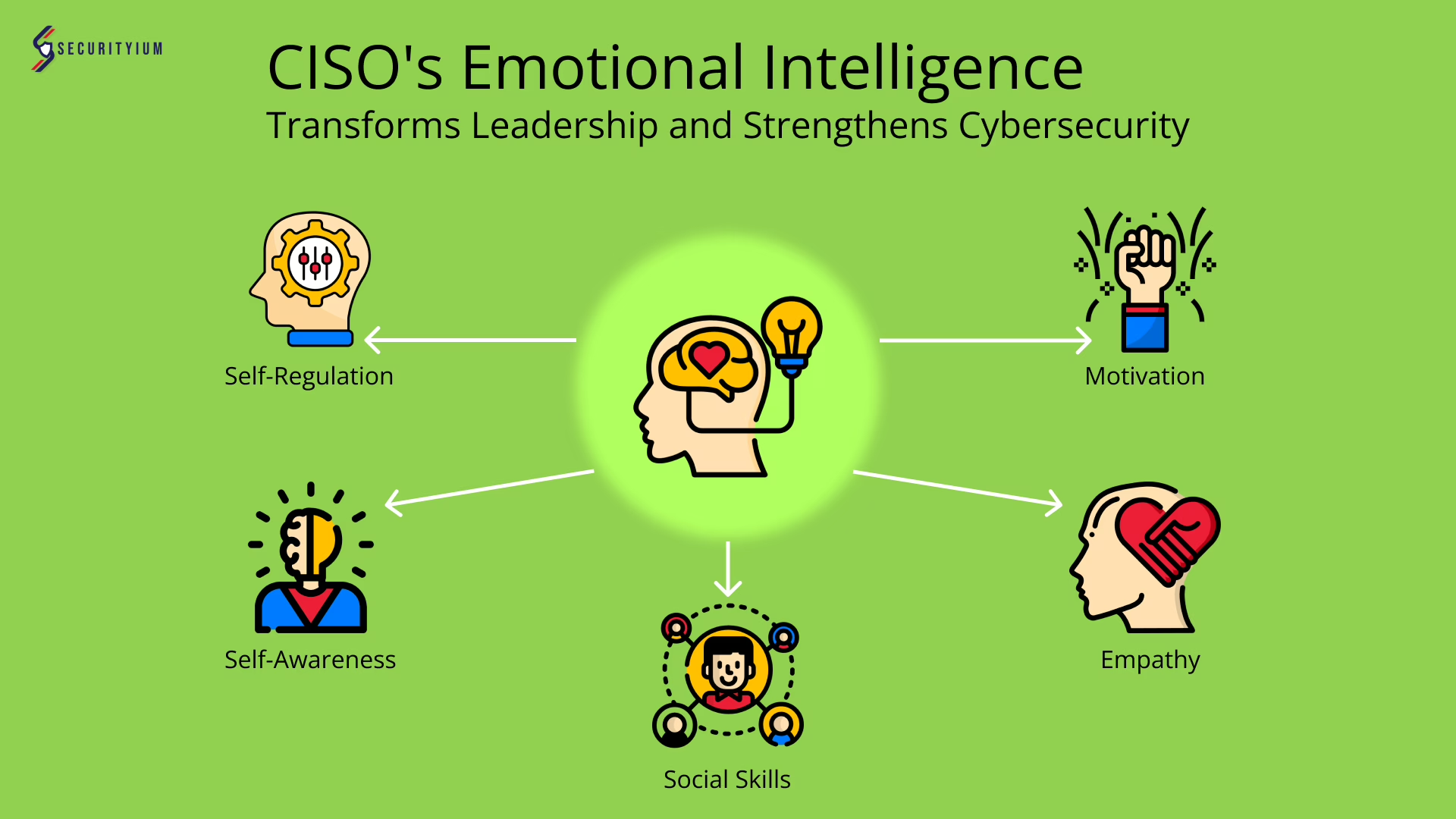
How CISO’s Emotional Intelligence Transforms Leadership and Strengthens Cybersecurity
Dec 2, 2024 Information hub
Learn how CISO's emotional intelligence boosts leadership, enhances communication, and builds a strong security culture in evolving cyber landscapes.

Product Security Best Practices for Safer Products
Dec 3, 2024 Information hub
Explore product security best practices to protect data, maintain trust, and prevent risks throughout your product's lifecycle, from design to decommissioning.

Cookies vs Supercookies: The Hidden Layers of Online Tracking
Dec 5, 2024 Information hub
Discover the differences between cookies vs supercookies, their privacy implications, and how to protect your data while browsing the web securely.
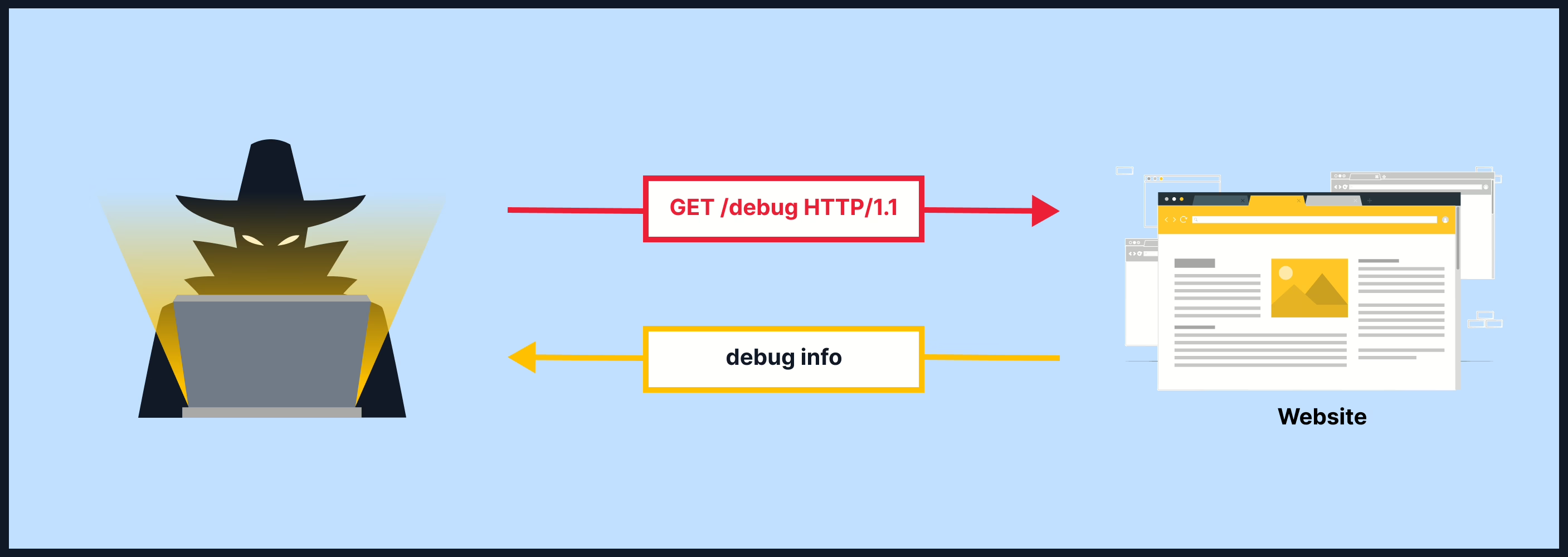
Understanding Information Disclosure Vulnerabilities: Risks & Fixes
Dec 11, 2024 Information hub
Explore what information disclosure vulnerabilities are, their risks, real-world examples, and how to prevent them with secure coding and system practices.

A Comprehensive Guide to OWASP Top 10 LLM Applications 2025
Jan 15, 2025 Information hub
Dive into the OWASP Top 10 LLM Applications 2025 to understand key vulnerabilities, trends, and mitigation strategies for secure AI systems.

Strategies to Mitigate LLM01:2025 Prompt Injection Risks
Jan 16, 2025 Information hub
Learn effective strategies to mitigate LLM01:2025 Prompt Injection risks and secure your large language model applications against evolving threats.

Addressing LLM02:2025 Sensitive Information Disclosure Risks
Jan 16, 2025 Information hub
Learn how to address LLM02:2025 Sensitive Information Disclosure, a critical vulnerability in large language models, and protect sensitive data effectively.

Addressing LLM03:2025 Supply Chain Vulnerabilities in LLM Apps
Jan 16, 2025 Information hub
Learn how to address LLM03:2025 Supply Chain vulnerabilities in Large Language Model applications. Discover key risks, mitigation strategies, and best practices for securing AI systems.
LLM04: Data and Model Poisoning in LLM Applications
Jan 16, 2025 Information hub
Discover the risks of LLM04: Data and Model Poisoning in LLM Applications, its impact on AI security, and proven mitigation strategies.

LLM05:2025 Improper Output Handling in LLM Applications
Jan 16, 2025 Information hub
Learn about LLM05:2025 Improper Output Handling in LLMs & discover key strategies to ensure secure & reliable output for AI systems.

Understanding LLM06:2025 Excessive Agency Risks
Jan 17, 2025 Information hub
Explore the LLM06:2025 Excessive Agency risk in LLM applications, its implications, & effective mitigation strategies for secure AI systems.

Protecting Against LLM07:2025 System Prompt Leakage
Jan 17, 2025 Information hub
Learn how to safeguard AI systems against LLM07:2025 System Prompt Leakage, a critical vulnerability in modern LLM applications, with actionable strategies.

A Guide to Mitigating LLM08:2025 Vector and Embedding Weaknesses
Jan 17, 2025 Information hub
Learn how to secure vectors and embeddings in LLM applications by addressing LLM08:2025 vector and embedding weaknesses for safer AI systems.

A Comprehensive Guide to Address LLM09:2025 Misinformation
Jan 17, 2025 Information hub
Learn how to tackle misinformation propagation in LLMs. Explore LLM09:2025 Misinformation risks, strategies, and future trends.

LLM10:2025 Unbounded Consumption: Managing Resource Risks
Jan 17, 2025 Information hub
Learn how to manage LLM10:2025 Unbounded Consumption risks in AI models. Explore causes, mitigation strategies, and trends.
Understanding Adversarial Attacks on AI Models: Risks & Solutions
Jan 30, 2025 Information hub
Learn how adversarial attacks on AI models exploit vulnerabilities, their real-world impact, and effective strategies to enhance AI security.
AI-Powered Applications and OWASP Standards for Security
Jan 30, 2025 Information hub
Discover how AI-powered applications and OWASP standards help mitigate security risks, ensuring data protection and compliance.
Best Practices for AI Risk Management: Key Strategies & Trends
Jan 30, 2025 Information hub
Discover the best practices for AI risk management, including governance, bias mitigation, security, and compliance for responsible AI use.
Data Poisoning in Generative AI: Risks, Examples & Solutions
Jan 30, 2025 Information hub
Learn about data poisoning in generative AI, its risks, real-world examples, and solutions to protect AI models from manipulation.
Emerging Threats in Generative AI Security: Risks & Solutions
Jan 30, 2025 Information hub
Explore emerging threats in generative AI security, including deepfakes, phishing, and adversarial AI, with solutions to mitigate risks.
Ethical AI in Generative Models: Challenges, Trends & Solutions
Jan 30, 2025 Information hub
Explore Ethical AI in Generative Models—key challenges, trends, and solutions to ensure responsible AI development and deployment.
Generative AI Security Challenges: Risks, Trends & Solutions
Jan 30, 2025 Information hub
Explore generative AI security challenges, including deepfakes, data privacy, and cyber threats, with key trends and solutions for safer AI adoption.
Managing Bias in AI Applications: Strategies & Practical Insights
Jan 30, 2025 Information hub
Explore managing bias in AI applications, its impact across industries, and practical strategies for building fair, inclusive, and trustworthy AI systems.
Mitigating Risks in Gen AI Applications: A Guide to Responsible Use
Jan 30, 2025 Information hub
Learn about mitigating risks in Gen AI applications, including bias, misinformation, privacy concerns, and effective solutions for risk management.
Privacy Risks in Generative AI Systems: Challenges & Solutions
Feb 5, 2025 Information hub
Explore key privacy risks in generative AI systems, including data leaks and deepfakes, and discover solutions to protect user data.
Why Regulatory Compliance for Generative AI Matters?
Feb 5, 2025 Information hub
Explore regulatory compliance for generative AI, its challenges, legal risks, and steps businesses can take for responsible AI innovation.
The Critical Need for Securing Gen AI in Enterprise Systems
Feb 5, 2025 Information hub
Learn key risks, trends, and best practices for securing Gen AI in enterprise systems to protect data, models, and compliance.
Why Trust and Transparency in AI Systems Matter Today
Feb 5, 2025 Information hub
Discover why trust and transparency in AI systems are essential, explore key challenges, trends, and solutions shaping ethical AI adoption.
AI Vulnerabilities in Large Language Models: Risks & Solutions
Feb 5, 2025 Information hub
Explore AI vulnerabilities in large language models, their risks, real-world examples, and solutions to ensure safe and ethical AI use.
AI Excessive Agency Risks in LLMs: Challenges & Solutions
Feb 5, 2025 Information hub
Understand AI excessive agency risks in LLMs, their challenges, real-world examples, and actionable solutions to ensure responsible AI use.
Future Trends in LLM Security: Key Challenges & Solutions
Feb 5, 2025 Information hub
Explore future trends in LLM security, key challenges, and innovative solutions to protect AI systems from threats and vulnerabilities.
Improper Output Handling in LLMs: Risks, Challenges & Solutions
Feb 5, 2025 Information hub
Learn about improper output handling in LLMs, its risks, real-world cases, challenges, and solutions for safe and reliable AI deployment.
LLM Data Model Poisoning: Risks, Challenges & Prevention
Feb 5, 2025 Information hub
Learn about LLM Data Model Poisoning, its risks, real-world impact, and effective strategies to prevent adversarial attacks on AI systems.
LLM Misinformation Challenges: Risks, Trends & Solutions
Feb 5, 2025 Information hub
Explore LLM Misinformation Challenges, including hallucination, bias, and detection issues. Learn solutions to address risks and ensure accurate AI outputs.
LLM Misinformation Propagation: Challenges, Risks & Solutions
Feb 5, 2025 Information hub
Explore the challenges of LLM Misinformation Propagation, including bias, hallucination, and amplification, and learn effective solutions to mitigate risks.
LLM OWASP Top 10 Vulnerabilities: Securing AI Systems Effectively
Feb 5, 2025 Information hub
Explore the LLM OWASP Top 10 Vulnerabilities, their impact on AI security, and practical strategies to mitigate these risks and safeguard sensitive data.
Understanding the OWASP LLM Top 10: Securing AI Systems
Feb 5, 2025 Information hub
Explore the OWASP LLM Top 10 vulnerabilities, their impact on AI security, and practical solutions to mitigate risks and protect LLM-powered systems.
OWASP Top 10 for LLM Applications: Key Security Risks
Feb 7, 2025 Information hub
Discover the OWASP Top 10 for LLM, the biggest security risks in Large Language Models, and strategies to mitigate vulnerabilities effectively.
OWASP Top 10 for LLM Applications: Security Tips
Feb 7, 2025 Information hub
Learn about the OWASP Top 10 for LLM Applications, key security risks, and best practices to protect AI systems from vulnerabilities.
OWASP Top 10 LLM Vulnerabilities: Key Risks & Solutions
Feb 7, 2025 Information hub
Explore the OWASP Top 10 LLM Vulnerabilities, their risks, real-world examples, and actionable solutions to secure AI-powered applications.
Prompt Injection in LLMs: Risks, Examples & Mitigation
Feb 7, 2025 Information hub
Learn about Prompt Injection in LLMs, its risks, real-world examples, and key strategies to mitigate this growing AI security threat.
Protecting Sensitive Data in LLM Training
Feb 7, 2025 Information hub
Protecting sensitive data in LLM training is crucial for security and compliance. Learn risks, solutions, and best practices to stay safe.
Responsible AI for LLMs: Ensuring Ethical and Fair AI Systems
Feb 7, 2025 Information hub
Discover how Responsible AI for LLMs ensures fairness, transparency, and accountability in AI systems for a safer digital future.
Secure Development for LLM Applications: Best Practices & Trends
Feb 7, 2025 Information hub
Learn secure development for LLM applications, key risks, best practices, and trends to build secure, compliant, and trustworthy AI solutions.
Sensitive Information Disclosure in LLM: Risks & Solutions
Feb 7, 2025 Information hub
Learn how to prevent Sensitive Information Disclosure in LLM. Explore risks, real-world cases, and solutions for AI data security.
System Prompt Leakage in LLMs: Risks, Causes & Solutions
Feb 7, 2025 Information hub
Learn about system prompt leakage, its risks, real-world cases, and solutions to secure AI models from unintended data exposure.
Unbounded Consumption in AI Models: Challenges & Solutions
Feb 7, 2025 Information hub
Unbounded consumption in AI models drives high data, computation, and energy use. Learn its impact, challenges, and sustainable solutions.
Vector and Embedding Security: Protecting LLMs from Threats
Feb 7, 2025 Information hub
Learn about Vector and Embedding Security, its risks, challenges, and solutions to safeguard LLMs from adversarial attacks and data breaches.
AI Cybersecurity: Securing AI Systems in 2025
Feb 25, 2025 Information hub
Explore AI cybersecurity in 2025 with the guide to secure AI systems. Learn key principles, real-world scenarios, and recent threats.
AI Cyber Security: UK’s 2025 Code of Practice Unveiled
Feb 25, 2025 Information hub
Discover the UK’s 2025 AI cyber security Code of Practice. Explore 13 principles, real-world applications, and recent threats in this guide.
Microsoft Quantum Chip: Quantum Computing in 2025
Feb 26, 2025 Information hub
Discover the Microsoft quantum chip, Majorana 1, and its topological qubits revolutionizing quantum computing in 2025.

Microsoft Majorana 1: The Next Big Thing in Quantum Tech
Feb 26, 2025 Information hub
Meet Microsoft Majorana 1, a new quantum chip that’s stable and strong, ready to change tech in 2025.
Quantum Chip: The Heart of Next-Gen Computing
Feb 28, 2025 Information hub
Curious about a quantum chip? Learn what it is, how it works, and why it could revolutionize computing with speed and power.

Quantum Computing History: Evolution to Microsoft Majorana 1
Feb 28, 2025 Information hub
Explore quantum computing history, from early theories to Microsoft’s Majorana 1. Learn how this tech grew into a game-changer over decades.
Topological Qubits Explained: The Science Behind Majorana 1
Mar 3, 2025 Information hub
Dive into topological qubits, the stable science behind Microsoft’s Majorana 1. Learn how they work and why they’re a quantum breakthrough.
Quantum Computing Rivals: Microsoft, Google & IBM
Mar 3, 2025 Information hub
Explore quantum computing rivals—Microsoft, Google, and IBM. Learn how they compare in stability, scale, and future impact.
Topoconductors: Driving Quantum Innovation Forward
Mar 3, 2025 Information hub
Learn how topoconductors fuel quantum innovation. Explore their role in Microsoft’s Majorana 1 and the future of stable quantum tech.
Quantum Cybersecurity: How Quantum Computing Reshapes Security
Mar 3, 2025 Information hub
Explore quantum cybersecurity and how quantum computing could break encryption and spark new defenses in this evolving tech landscape.
Microsoft Quantum Journey: 20 Years to Majorana 1
Mar 3, 2025 Information hub
Explore Microsoft quantum journey—20 years of innovation leading to Majorana 1. Dive into their bold quest for quantum tech supremacy.
Million Qubits: Why Quantum Chips Need This Goal
Mar 3, 2025 Information hub
Discover why million qubits is the quantum holy grail. Learn how Majorana 1’s aim could unlock breakthroughs in computing power.

Understanding HTTP Cookie Attributes: Security Risks and Bypass Techniques
Mar 9, 2025 Information hub
Cookies are used for session management, authentication, tracking, and user preferences in web applications. Secure cookies rely on attributes to protect against attacks like XSS, CSRF, and session hijacking.

Quantum Skepticism: Is Majorana 1 Overhyped?
Mar 10, 2025 Information hub
Dive into quantum skepticism around Majorana 1. Are Microsoft’s 2025 claims too bold? Experts weigh in on its potential and pitfalls.

Azure Quantum: Bringing Majorana 1 to the Cloud
Mar 10, 2025 Information hub
Learn how Azure Quantum aims to integrate Majorana 1, Microsoft’s quantum chip, into the cloud for groundbreaking computing power.

What is SQL injection (SQLi)?
Mar 17, 2025
Discover what is SQL injection (SQLi)? Learn how this web vulnerability works, its impact, real-world examples, and how to prevent it.

What are authentication vulnerabilities?
Mar 17, 2025 Technical Write ups
Explore authentication vulnerabilities, their impact, real-world examples, and how to prevent them. Learn key strategies to secure a website.

Understanding Web LLM Attacks
Mar 17, 2025 Technical Write ups
Web LLM attacks: Learn how attackers exploit large language models, real-world examples, and proven defenses to secure your website in 2025.

What is Path Traversal?
Mar 17, 2025 Technical Write ups
Explore path traversal vulnerabilities: how they work, real-world impacts, and proven prevention strategies to secure your web applications.

What Is OS Command Injection?
Mar 17, 2025 Technical Write ups
Dive into OS command injection: how it works, its devastating impact, and key prevention strategies to secure your web applications in 2025.

What are business logic vulnerabilities?
Mar 18, 2025 Technical Write ups
Business logic vulnerabilities: their causes, impacts, and prevention strategies to secure your applications. Real examples included.

Understanding Information Disclosure Vulnerabilities
Mar 18, 2025 Technical Write ups
Explore information disclosure vulnerabilities: what they are, their impact, and how to prevent them. Learn with examples and best practices.

Mastering Access Control Vulnerabilities and Privilege Escalation
Mar 18, 2025 Technical Write ups
Learn about access control vulnerabilities and privilege escalation: types, risks, and prevention. Practical examples and tips included.

What Are File Upload Vulnerabilities?
Mar 18, 2025 Technical Write ups
Discover file upload vulnerabilities: risks, exploits like web shells, and prevention tips. Stay secure with examples and best practices.

Exploring Server-Side Request Forgery (SSRF)
Mar 18, 2025 Technical Write ups
Server-side request forgery (SSRF): risks, exploits like localhost attacks, and prevention tips. Secure your apps with expert insights.
Protect your business assets and data with Securityium's comprehensive IT security solutions!

